


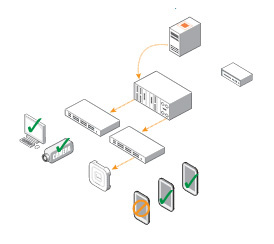
Automate your endpoint security policies to control access by user, location and time.
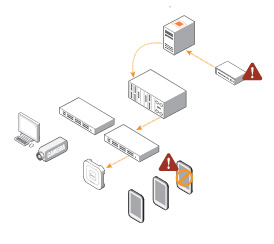
Devices with suspected threats, malware and ransomware are automatically isolated from the rest of the network to limit damage.
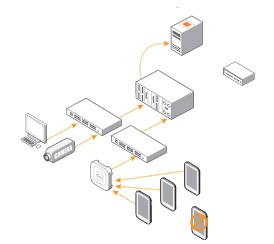
Control what connects to your network with an automatic whitelist of known devices to simplify authentication and exclude threats.




