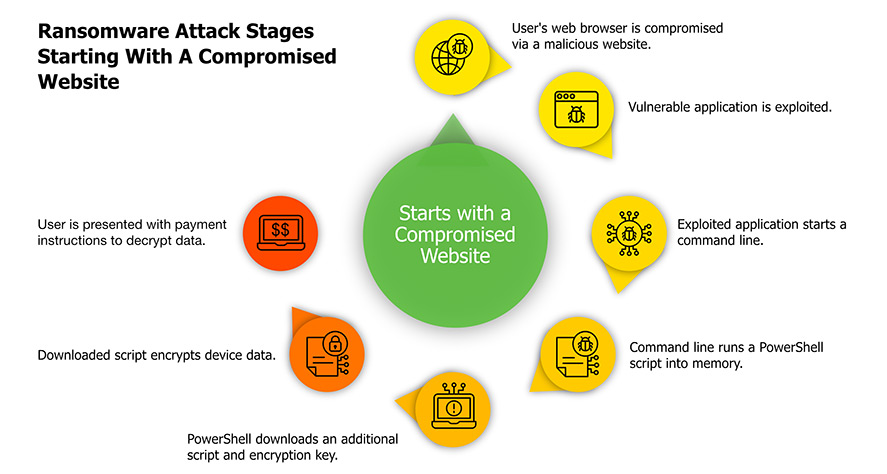
Targeted ransomware attacks against government bodies, schools, universities, corporations, service providers, and even small-medium businesses have been steadily increasing over the years. Like evolution of malware, ransomware attacks have also progressed from simple to more sophisticated attacks that may spread over a network and use worms (ransomworm or cryptoworm) to increase hostages and monetary profits. Ransomwares such as Ryuk are frequently triggered by sophisticated trojans such as Emotet, which perform evasive operations and even delete backups, such as shadow files, on hosts/servers in order to maximize damage and prevent recovery by other ways without a payout. WannaCry, CryptoLocker, Ryuk, Petya, notPetya, and Maze are some of the well-known ransomwares that have caused significant damage.
Each step of a ransomware attack may usually be identified as a suspicious threat indication, leading to the possibility of a ransomware attack by various protection solutions. However, the following are the challenges in identifying and combating ransomware with existing security tools.
Detecting ransomware requires a high level of dependence on behavioral analytics and threat modelling. Traditional threat detection technologies rely significantly on the security analyst to find out anomalous behavior and to establish correlation rules to connect the indicators together.This method heavily weighs on the analyst’s ability to detect threats and navigate a complicated user interface, giving room for subjectivity in achieving the intended result. aiSIEM/aiXDR, on the other hand, relies on Machine Learning for behavioral analytics and Artificial Intelligence for correlating indicators driven by built-in dynamic threat models. The algorithm provides an alert for the analyst to act on when these indicators match up with a particular degree of certainty.
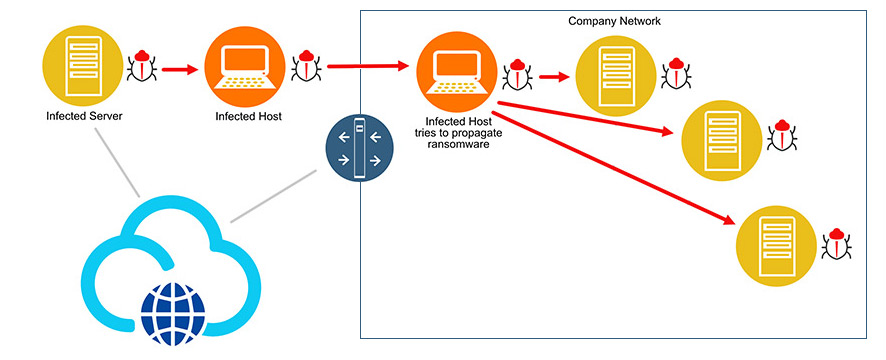
Detection at the Host: The ransomware payload attempts to reach the endpoint host. In the event of an email phishing attempt, aiSIEM/aiXDR reacts rapidly, correlating email server logs with endpoint activities to look for indications of odd or suspicious processes created on the endpoint.
Detection at the Host Connecting with the (C&C): The malware attempts to connect to the Command-and-Control Center (C&C) from the affected host. It may potentially generate a new domain and try to connect to it. aiSIEM/aiXDR technology steps in to detect the auto-generated domain names and correlate that information with other threat indicators in order to issue an alert.
Lateral Movement Detection: When an infected host is introduced into a network, the malware may run a network scan to discover potential targets before spreading to other endpoints/servers like a worm. aiSIEM/aiXDR can quickly identify this behaviour and connect it with contextual events, triggering a “Potential Malware Infected Host” warning and quarantining the infected host.