

By providing on-premises, cloud-based and as-a-service options, SonicWall helps you deploy what works for your architecture and evolve secure cloud adoption at your pace.
Mix and match security products to create or enhance cloud-native and hybrid deployment models that fit your current needs and bridges a path to a more virtualized reality.
Leverage modern zero-trust capabilities to easily and quickly connect remote users to on-premises resources, cloud-hosted applications, branch offices and public clouds — all without installing hardware.
Safeguard remote employees and mobile workers with virtualized security options. Easily deploy security across multiple locations — with minimal IT support — using Zero-Touch Deployment capabilities.
Manage remote users, devices and applications from anywhere in the world. SonicWall’s cloud-native architecture eliminates the need to service physical appliances, schedule downtime and build out expensive redundancies.
Secure common SaaS applications with a single security tool that requires no hardware or software installation. Quickly protect users, regardless of location, with convenient API connections to business-critical SaaS applications, including G Suite, Office 365 and more.
Protect your organization, networks, users and devices on your terms. Explore real-world use cases that showcase the power and flexibility of scaling proven security across even the most complex cloud-native and hybrid environments.
Secure access to cloud and on-premises applications and virtualized workloads through modern zero-trust capabilities.
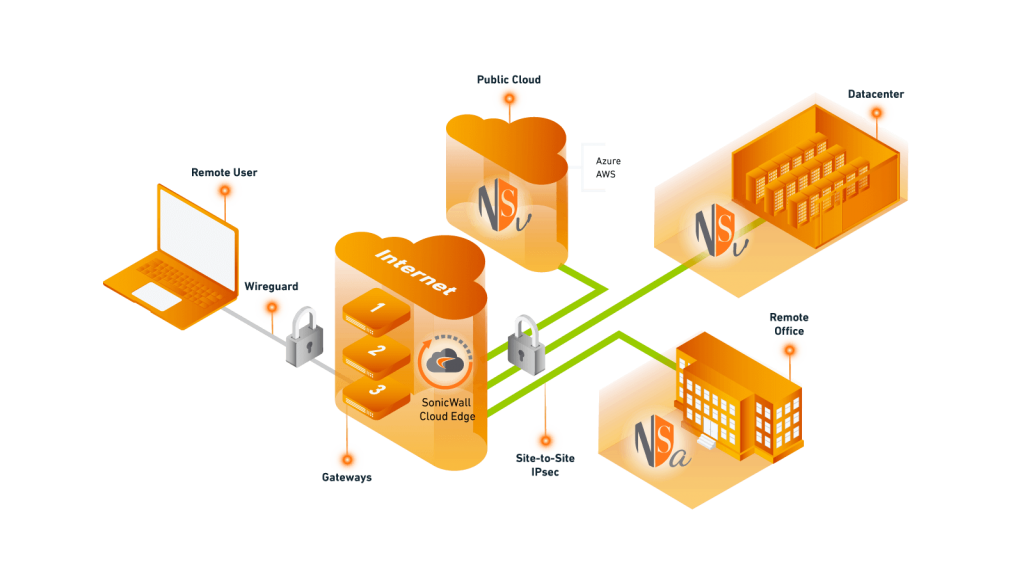
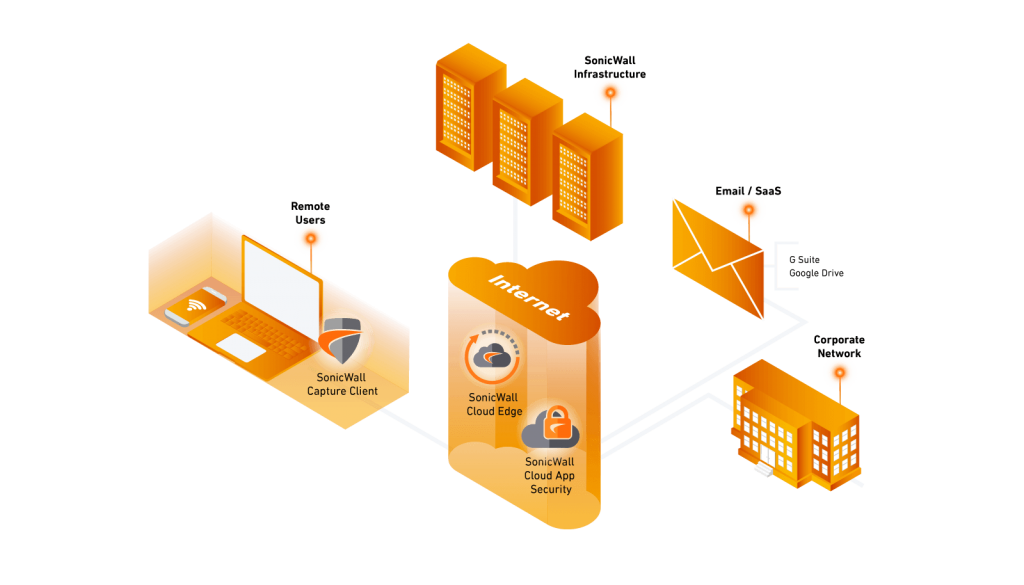
Solve security and connectivity challenges for cloud migration.
Protect distributed and remote workforces through powerful virtualized security layers and zero-touch capabilities.
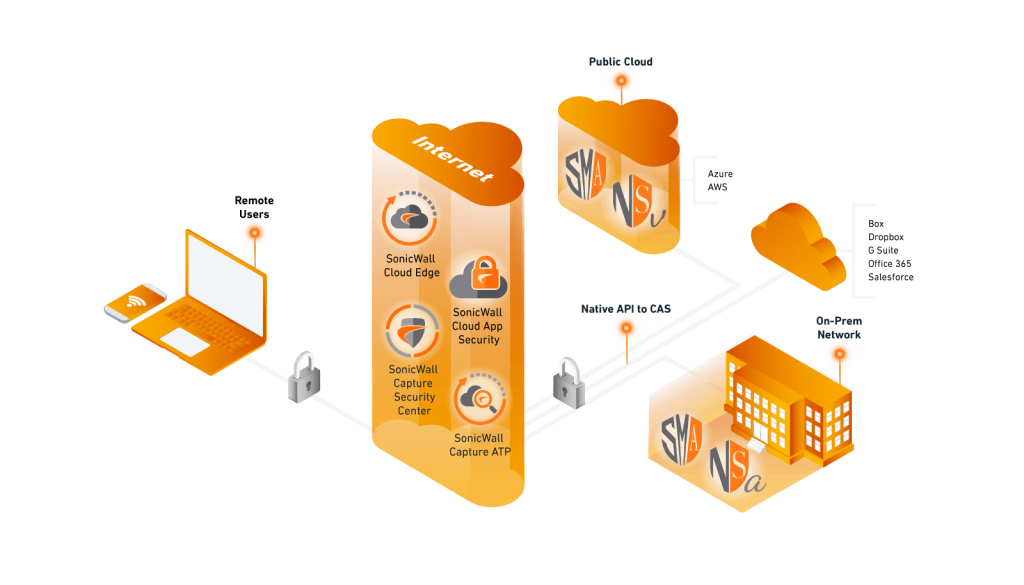
In less than 15 minutes, SonicWall Cloud Edge Secure Access quickly scales security beyond your perimeter through modern zero-trust principles. Establish logical trust zones to securely authenticate every user, device and location for access only to the specific services and resources required.
